Over 140 ransomware families down – No More Ransom celebrates its fourth anniversary
Riyadh – ![]() :
:
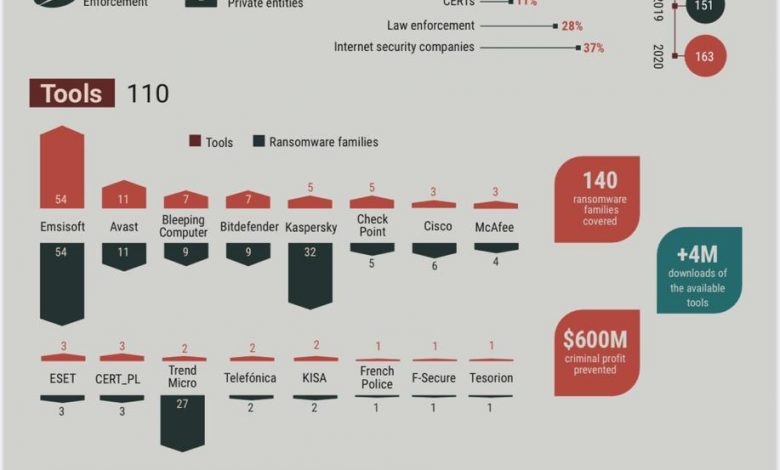
In July 2016, the No More Ransom initiative was launched by the Dutch National Police, Europol, McAfee and Kaspersky. Today there are 163 partners all over the world. The portal has added 28 tools in the past year and can now decrypt 140 different types of ransomware infections. The portal is available in 36 languages.
Over just the last two years, Kaspersky decryptors, posted on the NMR website, were downloaded over 216,000 times. Of those, the two most popular decryptors were WildFireDecryptor and CoinVaultDecryptor. Both of them are focused on helping victims of the relevant ransomware family recover their data. You can learn more here and here.
Celebrating its fourth anniversary this month, the No More Ransom decryption tool repository has registered over 4 million visitors from 188 countries since its launch and has stopped an estimated $600 million in ransom demands from ending up in criminals’ pockets.
“The success of the No More Ransom initiative is a shared success, one that cannot be achieved by law enforcement or private industry alone. By joining forces, we enhance our ability to take on the criminals and make it harder for them to harm people, businesses and critical infrastructure. What ransomware has taught us for sure is that prevention is no doubt better than a cure. Internet users need to avoid becoming a victim in the first place. Many relevant prevention tips are available on the No More Ransom website. If you do become a victim, it is important not to pay the ransom and report your infection to the police,” said Fedor Sinitsyn, security expert at Kaspersky.
Among other new ways to use malware extortion is by exploiting unreliable passwords for Remote Desktop Protocols (RDPs) and subsequently remotely launching the decryptor.
In this regard, it is extremely important to use strong passwords for accounts, and it is also recommended not to allow open access via RDP for online connections – instead, use a connection to the corporate network via VPN.
More prevention tips and information here.




